Lets be up front
You have a business to run.
But the world has changed and is changing at such a rapid pace how can you keep up.
Technology comes and goes so fast, when is it more expensive to stay with what you have than it is to upgrade? If so what gives you the best bang for the buck.
Why are we different?
We treat everything as if it were our company. Would I do this if I was cutting the check.
We are not looking to lock you into a recurring service charge, we want to be who you call when you need us.
We do not focus on selling you any software or hardware, we will connect you with who you can get the best price for what you need and you buy from them direct.
while we can provide some solutions directly, our focus is on what is the best fit for you and your company. We dont broker back end deals with the vendors, we are truly vendor neutral.
We are a Microsoft partner, thats because thats what we use to run our business, but believe in the right tool for the job.
We are now a Sophos partner, because this is what we use to run our business. Our focus is not to "Sell" you products, we want to work with you to find the best solution for your needs
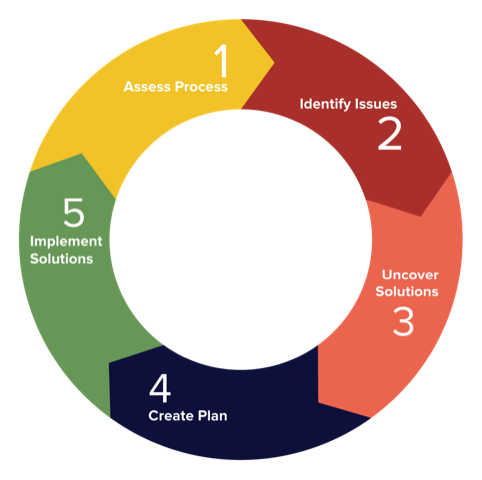
How we operate
First and foremost learn your business and its needs.
- Initial Assessment of where you are today
- Quick discussion on where you want to go
- Basic information on risks
- Evaluate systems
- Propose solution, defining risk and reward for each part
So contact us to find out more
Why
Choose Us?
We arent here to tell you what you want to hear.
We provide truthful assessment of your IT issues. But we also provide answers and options. What it takes to get you the results you need, without going broke.

How we look at things.
Its pretty simple, would I do what I am recommending if I am the one writing the check? The last thing you need is someone coming in that over sells and under delivers, we benefit by helping you, not selling you products and services.
The best questions to ask, are what are your pain points, what is stopping you from doing more. We look for the problem and give you options on how to take care of it.
Lets talk about this
The technology world has changed
-
The New Norm
-
Malware
-
Cyber Security
-
What do I ask
The New Norm
COVID-19 has changed the business and social landscape. Is this a temporary reality, or are you looking for this to be the "New Norm" and how do I as a business continue to function. Everything from restructuring your office, to remote work is being re-addressed. What works for you, we live in a connected world, Utilizing products like Microsoft Teams can help your company evolve. Can your operation benefit from this "New Norm", well lets talk about your business processes, your needs, and how you might move forward in this new world.

Malware
Malware is a generic term that is used to describe any software that is being used for a purpose with malicious intent. There are numerous types of malware
1. Viruses, A computer virus is what most of the media and regular end-users call every malware program reported in the news.
2. Worms, Worms have been around even longer than computer viruses, all the way back to mainframe days.
3. Trojans, Just like the trojan horse they appear to be a normal program but contain malicious instructions
4. Hybrids, they are usually a combination of trojans, and worms, and you may have heard of Bot Nets, this is a form of Hybrid
5. Ransomeware, Just like the name suggests, its a trojan thats been introduced to your system, through a variety of methods, and at a time when enough information has been gathered and communicated back to the command and control servers, it encrypts or makes your files unavailable unless you pay.
6. Fileless malware, is more of an exploit, where they try to execute and gain access through unprotected segments of your network
7. Adware, Most people have been hit with this sometime in the past, you open your browser to search for something and it redirects you to a different site
8. Malvertising, a form of adware, that compromises legitimate ads that then cause you to install a malware
9. Spyware, is used to capture information, maybe a keylogger, so as to find a way into a system, in a method that looks legitimate.
And guess what your phone, its vulnerable to alot of this as well, there is even another category of malware, called fleeceware, where you install an app that has authority to install other "Trial" software and then you get hit with high subscriptions after the trials run out.

Cyber Security
Cyber security is the practice of defending computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks. It's also known as information technology security or electronic information security. The term applies in a variety of contexts, from business to mobile computing, and can be divided into a few common categories.
Network security is the practice of securing a computer network from intruders, whether targeted attackers or opportunistic malware.
Application security focuses on keeping software and devices free of threats. A compromised application could provide access to the data its designed to protect. Successful security begins in the design stage, well before a program or device is deployed.
Information security protects the integrity and privacy of data, both in storage and in transit.
Operational security includes the processes and decisions for handling and protecting data assets. The permissions users have when accessing a network and the procedures that determine how and where data may be stored or shared all fall under this umbrella.
Disaster recovery and business continuity define how an organization responds to a cyber-security incident or any other event that causes the loss of operations or data. Disaster recovery policies dictate how the organization restores its operations and information to return to the same operating capacity as before the event. Business continuity is the plan the organization falls back on while trying to operate without certain resources.
End-user education addresses the most unpredictable cyber-security factor: people. Anyone can accidentally introduce a virus to an otherwise secure system by failing to follow good security practices. Teaching users to delete suspicious email attachments, not plug in unidentified USB drives, and various other important lessons is vital for the security of any organization.

What do I ask?
As a business owner you need to ask, what are my options?
What are the pros and cons?
What are the real costs?
In the current technology space we are in, you are going to be looking at cloud offerings, This is something to look at in depth.
The real question is does it fit your business, do parts of your business make sense to move to the cloud.
What do you currently have in use?
Are you going to have to replace your current technology?
If so would it be better for the CAPEX or OPEX expenditures?
Is this the time for a full tech refresh?
Do you have the resources to parrallel systems, financially and personnel.
So lets talk Zero Point Solutions wants to work with you to get the answers that are best for your business
© 2023 Zero Point Solutions


